TLS Certificates in K8S
how does certificates works in kubernetes?
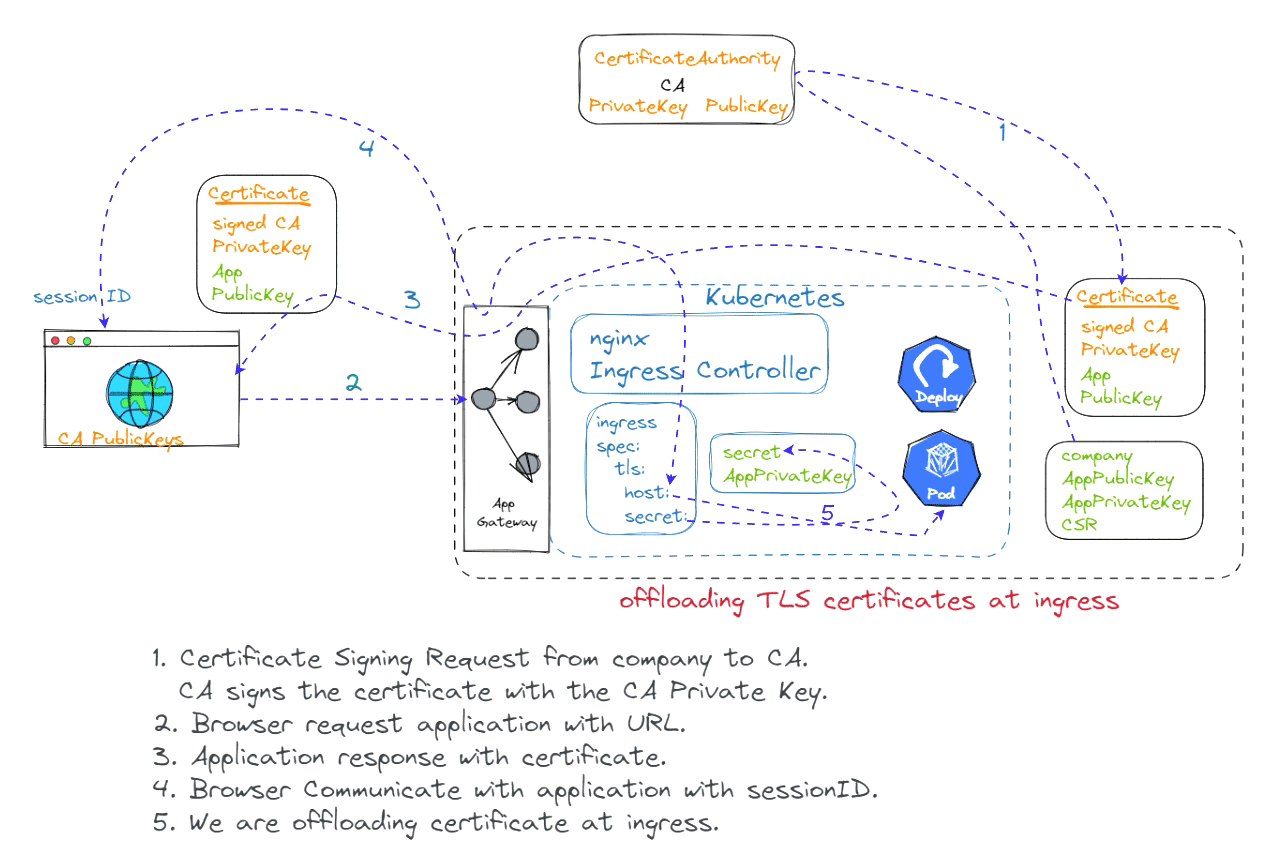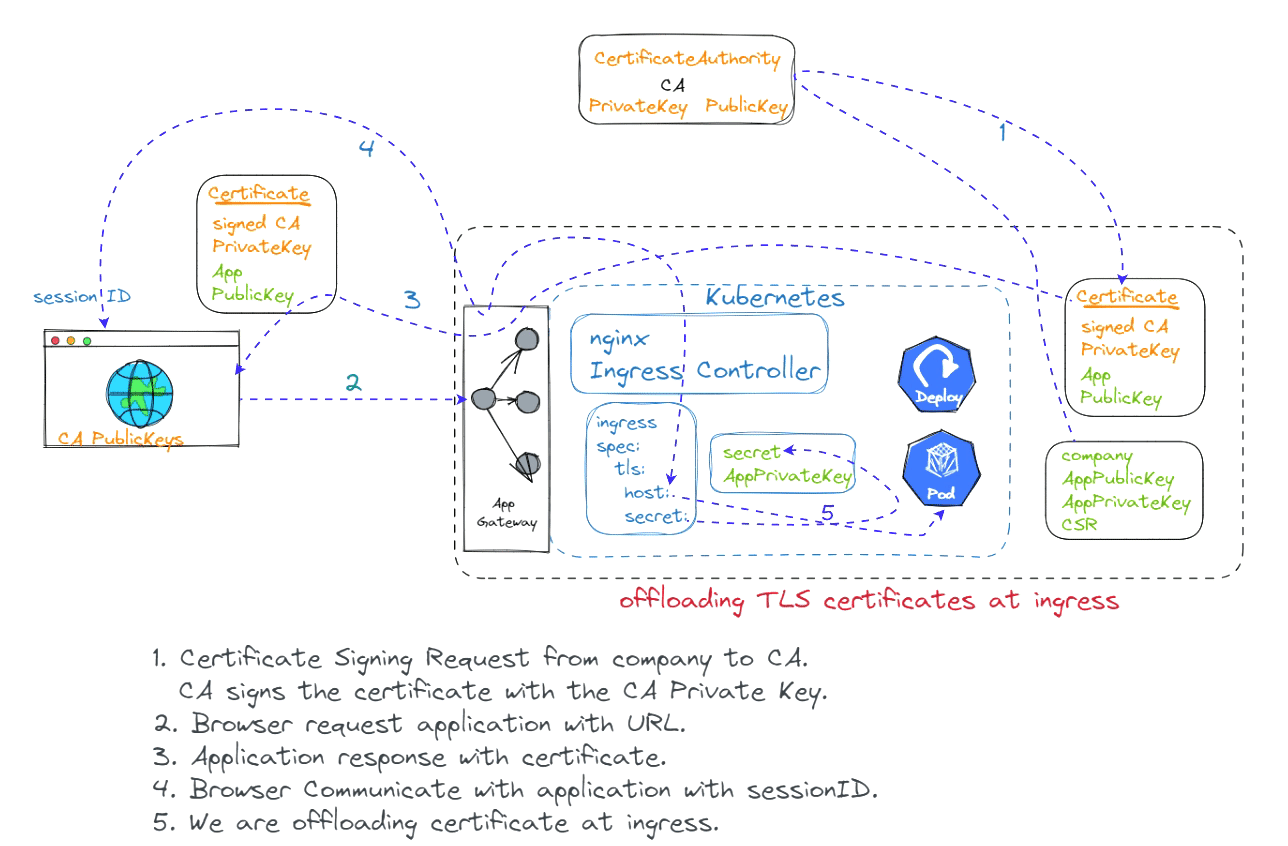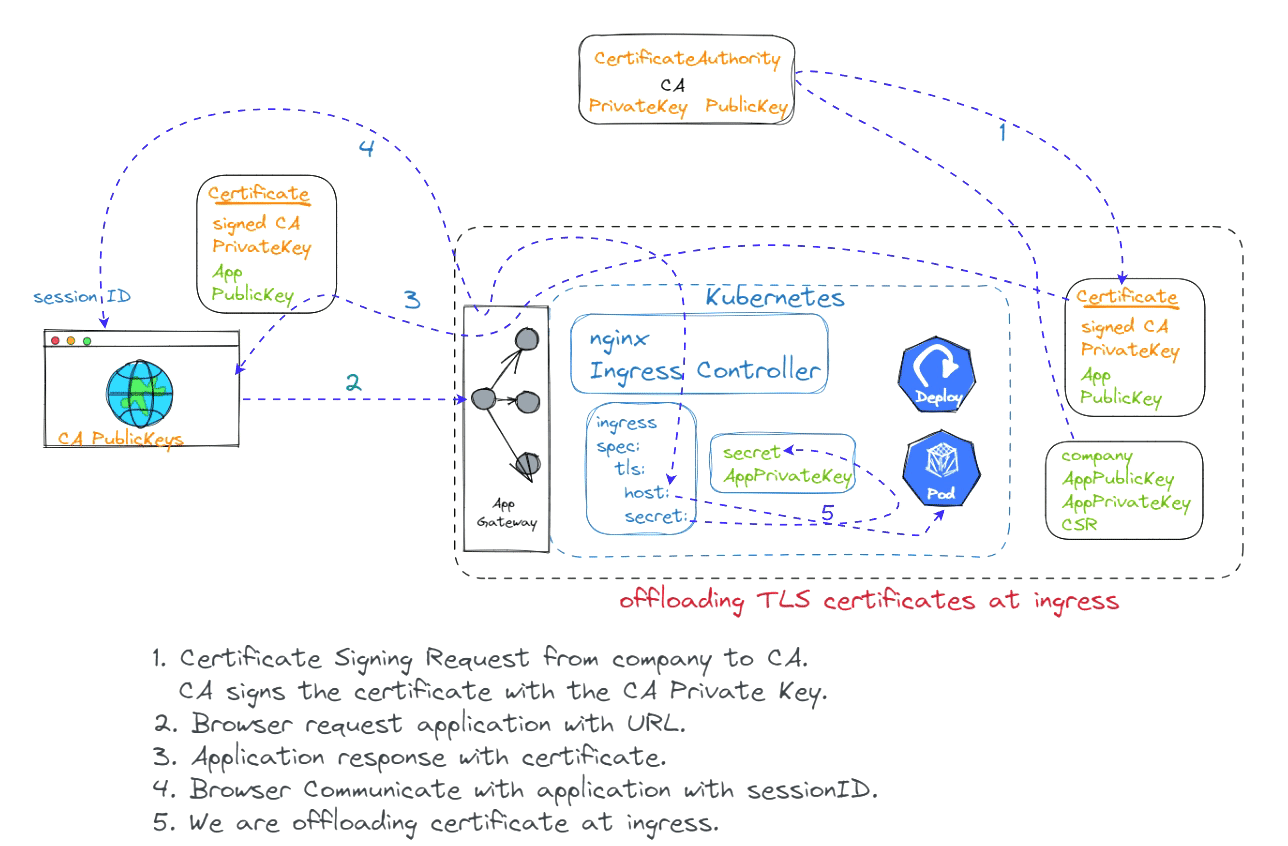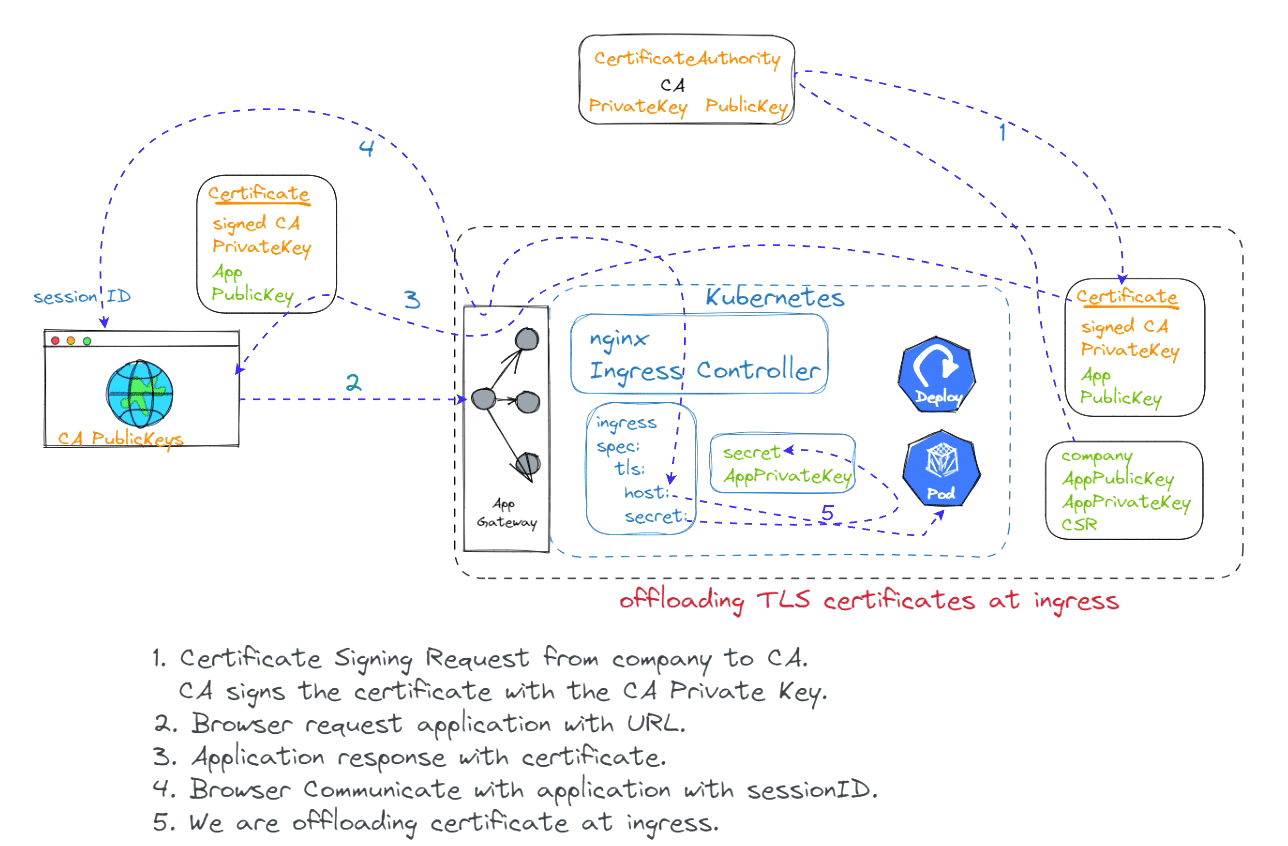
Offloading certificates to an ingress controller is a common practice that can improve the security and performance of your web applications. By offloading the certificates to the ingress controller, you can free up resources on your web servers and improve the overall performance of your applications.
To offload certificates to an ingress controller, you will need to create a certificate signing request (CSR) and submit it to a certificate authority (CA). Once the CA has issued the certificate, you can install it on the ingress controller.
The specific steps involved in offloading certificates to an ingress controller may vary depending on the ingress controller and the CA being used. However, the general steps are as follows:
Create a CSR.
Submit the CSR to the CA.
Install the certificate on the ingress controller.
Configure the ingress controller to use the certificate.
Here are some additional details about each of the steps involved:
Choosing a CA: When choosing a CA, it is important to consider factors such as the CA’s reputation, the types of certificates it offers, and its pricing. Some popular CAs include VeriSign, Thawte, and Comodo.
Creating a CSR: The CSR can be created using a variety of tools, such as the OpenSSL command-line tool or a web-based CSR generator. The CSR must contain the following information:
The name of the entity that is requesting the certificate.
The domain name for which the certificate is being requested.
The public key of the entity.
The signature algorithm that will be used to sign the certificate.
Submitting the CSR to the CA: The CSR can be submitted to the CA using a variety of methods, such as through a web portal, email, or FTP.
Installing the certificate on the ingress controller: The certificate must be installed in the correct location on the ingress controller. The specific location may vary depending on the ingress controller being used.
Configuring the ingress controller to use the certificate: The ingress controller must be configured to use the certificate. The specific configuration steps may vary depending on the ingress controller being used.
Once the certificates have been offloaded to the ingress controller, your web applications will be able to use the certificates to secure their connections. This will improve the security and performance of your web applications.
Consider subscribing my substack.